As stated in the ” Bitcoin White Paper “: The continued and steady growth of the amount of this new currency is similar to gold miners expending resources to increase the circulation of gold. For Bitcoin mining, the resources consumed are CPU computing time and electricity.
Bitcoin mining can be briefly summarized as follows:
- People compete to be rewarded with Bitcoin by applying computing power in a process called “Proof of Work” (PoW). This process is called “proof of work” because only those participants (miners) who prove they have put in enough resources (work) have a chance to win rewards.
- Approximately every 10 minutes, a winning “miner” will receive a reward.
- The rewards are twofold: (1) “Block Rewards”, which are newly issued Bitcoins. The block reward is currently set at 6.25 Bitcoins (but will be halved in early May 2024, then halved again four years later, and so on); (2) various transactions related to all transactions in the current block Handling fee.
Specifically, the process of Bitcoin mining is as follows:
- New transactions are broadcast to all nodes.
- Each node collects new transactions into a block.
- Each node looks for proof of work for its blocks.
- When a node finds the proof of work, it broadcasts the block to all nodes.
- Nodes will only accept a block if all transactions in the block are valid and have not been consumed before.
- Nodes indicate acceptance of the current block by creating the next block in the chain using the hash of the current block as the previous hash.
Proof of Work in Bitcoin
What is proof of work? Proof of work means proving that you have done a certain amount of work. For example, I studied for 50 hours at a driving school. And others can simply verify that workload. For example, showing your driver’s license means that you have indeed studied at a driving school for a period of time:
Bitcoin’s proof-of-work needs to come down to computer calculations, a.k.a. math problems. How to construct a mathematical problem to implement proof of work? Let’s look at a simple example.
Suppose that in a class at a certain school, there is only one girl named Xiaohong, and the others are boys. Every boy wants to ask Xiaohong to watch a movie, but only one boy can realize his wish. Which boy should you choose? In line with the principle of fairness, Xiaohong needs to test the sincerity of each boy. The method of testing is to ask a math problem, such as solving an equation. Whoever solves the equation first will be qualified to watch a movie with Xiaohong. Because there is no fixe formula for solving higher-order equations, a large amount of calculations are require to calculate the correct results. This calculation process requires a certain amount of work. Assuming that Xiao Ming is the first to calculate the result x=2.5, Xiao Hong can simply verify whether this result is correct.
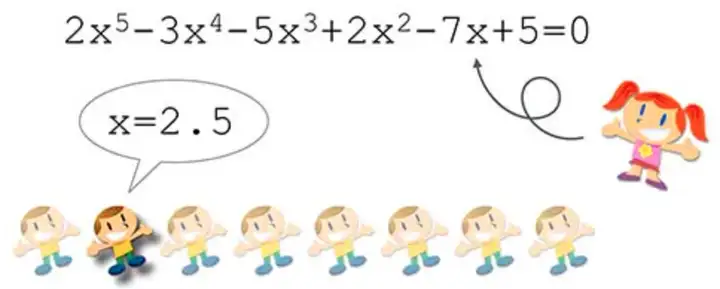
It can be see that solving the equation is difficult, but verifying the results is relatively simple. Therefore, an effective proof of work lies in the fact that the calculation process is very complex and takes a certain amount of time, but the verification process is relatively simple and can be complete almost instantly.
Now another question arises: What if someone else peeks at Xiao Ming’s answer and jumps in to answer it? It is also easy to solve this problem. Xiaohong can send different equations to different boys according to their numbers. The coefficient of the first term of the equation is the number. In this way, the equations that everyone needs to solve are different. The x=2.5 solved by Xiao Ming is invalid for Xiao Jun, because Xiao Jun’s number is 3. Using Xiao Ming’s results to verify Xiao Jun’s equation cannot pass the verification. In fact, if an equation is verified and passed, Xiaohong can directly know who solved the equation from the first coefficient of the equation. Therefore, it is useless to steal the results of other people’s proof of work.
Through proof of work, it can be effectively verified that everyone indeed must have spent a certain amount of time doing the calculations. In the Bitcoin network, miners’ mining is also a proof of work. However, it cannot be achieve by solving polynomial equations, because solving polynomial equations is difficult for humans to calculate, but it is very easy for computers. It can be do in 1 second. Completed within minutes. In order for the computer to implement workload proof, a workload algorithm must be found that the computer cannot calculate in a short time. This algorithm is a hash algorithm.
The proof-of-work principle of Bitcoin mining is to continuously try to calculate the hash of the block until a specific hash value is calculate. By changing the value of a nonce field in the header of the block, the computer can calculate different areas. Block hash:
Hash value
The calculation ends when a specific hash value is calculate. Compare with other hashes, this hash is characterize by several 0s in front:
hash256(block data, nonce=0) = 291656f37cdcf493c4bb7b926e46fee5c14f9b76aff28f9d00f5cca0e54f376f
hash256(block data, nonce=1) = f7b2c15c4de7f482edee9e8db7287a6c5def1c99354108ef33947f34d891ea8d
hash256(block data, nonce=2) = b6eebc5faa4c44d9f5232631f39ddf4211443d819208da110229b644d2a99e12
hash256(block data, nonce=3) = 00aeaaf01166a93a2217fe01021395b066dd3a81daffcd16626c308c644c5246
hash256(block data, nonce=4) = 26d33671119c9180594a91a2f1f0eb08bdd0b595e3724050acb68703dc99f9b5
hash256(block data, nonce=5) = 4e8a3dcab619a7ce5c68e8f4abdc49f98de1a71e58f0ce9a0d95e024cce7c81a
hash256(block data, nonce=6) = 185f634d50b17eba93b260a911ba6dbe9427b72f74f8248774930c0d8588c193
hash256(block data, nonce=7) = 09b19f3d32e3e5771bddc5f0e1ee3c1bac1ba4a85e7b2cc30833a120e41272ed
...
hash256(block data, nonce=124709132) = 00000000fba7277ef31c8ecd1f3fef071cf993485fe5eab08e4f7647f47be95cThe proof-of-work principle of Bitcoin mining is to continuously try to calculate the hash of the block until a specific hash value is calculated, which is smaller than the difficulty value.
The SHA-256 algorithm used by Bitcoin can be seen as producing random outputs for random inputs. For example, we calculate SHA-256 twice for the string Hello plus a number. Depending on the number, the resulting hash is completely irregular. 256-bit random number:
hash256("Hello8") = cf17d3f38036206cfce464cdcb44d9ccea3f005b7059cff1322c0dd8bf398830
hash256("Hello9") = 1f22981824c821d4e83246e71f207d0e49ad57755889874d43def42af693a077
hash256("Hello10") = 8a1e475d67cfbcea4bcf72d1eee65f15680515f65294c68b203725a9113fa6bf
hash256("Hello11") = 769987b3833f082e31476db0f645f60635fa774d2b92bf0bab00e0a539a2dede
hash256("Hello12") = c2acd1bb160b1d1e66d769a403e596b174ffab9a39aa7c44d1e670feaa67ab2d
hash256("Hello13") = dab8b9746f1c0bcf5750e0d878fc17940db446638a477070cf8dca8c3643618a
hash256("Hello14") = 51a575773fccbb5278929c08e788c1ce87e5f44ab356b8760776fd816357f6ff
hash256("Hello15") = 0442e1c38b810f5d3c022fc2820b1d7999149460b83dc680abdebc9c7bd65caeIf we want to find the hash value whose first two digits are 0, theoretically we need to calculate it 256 times, because the probability of 00 appearing is 162=256, and the actual calculation is 44 times:
hash256("Hello44") = 00e477f95283a544ffac7a8efc7decb887f5c073e0f3b43b3797b5dafabb49b5If we want to find the hash value whose first three digits are 0, theoretically we need to calculate 163 = 4096 times, but actually we need to calculate 6591 times:
hash256("Hello6591") = 0008a883dacb7094d6da1a6cefc6e7cbc13635d024ac15152c4eadba7af8d11cExample if we want to find the hash value whose first 4 digits are 0, theoretically we need to calculate 164 = 65,000 times, and actually we need to calculate it more than 67,000 times;
If we want to find the hash value whose first 5 digits are 0, theoretically we need to calculate 1.65 = 1.04 million times, and in practice we need to calculate 1.58 million times;
Example if we want to find the hash value whose first 6 digits are 0, theoretically we need to calculate 166 = 16.77 million times, and actually we need to calculate 15.58 million times;
The difficulty of the Bitcoin network is constantly changing. Its difficulty is guarantee to generate a block approximately every 10 minutes. And the difficulty value is adjust every 2015 blocks: If the average block generation time is less than 10 minutes, it indicates the computing power of the entire network As the number increases, the difficulty will also increase. If the average block generation time is greater than 10 minutes, it means that the computing power of the entire network will decrease and the difficulty will also decrease. Therefore, the difficulty will be dynamically adjust as the computing power of the entire network increases or decreases.
Base on the difficulty value and production time of each Bitcoin block. The computing power of the entire Bitcoin network can be calculate. The overall computing power of the Bitcoin network has been increasing rapidly. Currently, the computing power of the entire network has exceed 100EH/second, which means approximately 1 trillion hashes are calculate every second:
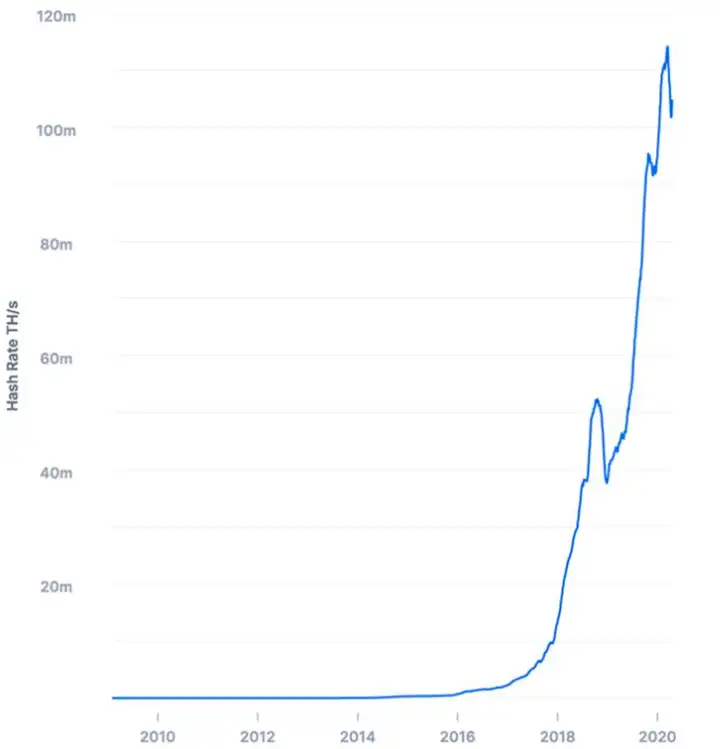
So Bitcoin’s proof-of-work is colloquially call mining. At the same time, all miners are working hard to calculate the hash of the next block. The mining difficulty depends on the percentage of the total computing power of the entire network. For example, assuming that Xiao Ming owns 1% of the total computing power of the entire network, then the possibility of him digging the next block is 1%. In other words, for every 100 blocks dug out, about 1 will be mine. of. Since the current computing power of the entire network exceeds 100EH/s, the computing power of a single machine’s CPU is only a few M, and the computing power of a GPU is only 1G, so the success rate of single-machine mining is almost equal to 0. Bitcoin mining has developed from early CPUs and GPUs to mining pools built with dedicated ASIC chips.
When a miner successfully finds a new block for a specific hash, he immediately broadcasts the block to the entire network. After receiving the new block, other miners will verify the new block and, if valid, add it to the end of the blockchain. At the same time, it shows that in this round of proof-of-work competition, this miner won, while other miners failed. The failed miner will abandon the block that it is currently calculating but has not yet completed, and start calculating the next block to compete in the next round of proof of work.
Why are blocks safe to broadcast? Because Merkle Hash locks all transactions in this block. And the first coinbase transaction output address of this block is the miner’s address. The block data generated by each miner when mining is different, so it is impossible to steal other people’s workload.
The total amount of Bitcoin is limited to approximately 21 million Bitcoins. And the initial mining reward is 50 Bitcoins per block, which will be halve every 4 years.
Hash Algorithm in Bitcoin
Bitcoin uses a military-grade encryption algorithm called Secure Hash Algorithm 2 (SHA2). Bitcoin miners are reward with Bitcoins when they find a random number. That can only be generate by running a hashing algorithm. This process is essentially a computational lottery and requires a lot of computing power.
Consensus Algorithm in Bitcoin
If two miners each find a valid block at the same time, note that the two blocks are different. Because the coinbase transactions are different, so the Merkle Hash is different and the block hash is also different. But they are all valid as long as they meet the difficulty value. At this time, which block should other miners on the network receive and add to the end of the blockchain? The answer is, it’s possible.
Usually, miners receive the valid blocks received first. Since the order of P2P network broadcast is uncertain, it is possible that different miners receive different blocks first. At this time, we say that the block has forked. In the case of a fork, some miners continue to mine on the green fork. And some miners continue to mine on the blue fork:
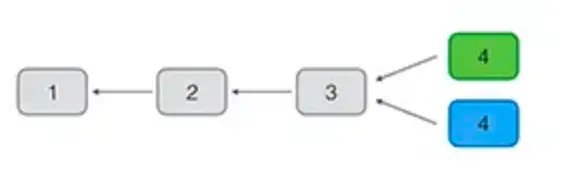
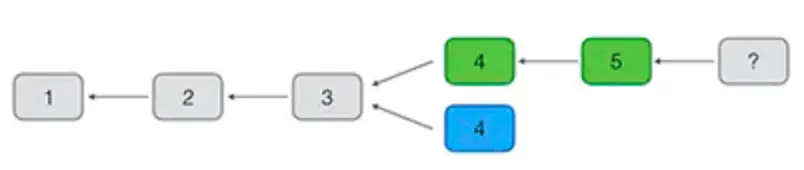
But in the end, there is always a fork that mines the subsequent blocks first. At this time, because the Bitcoin network adopts the consensus algorithm of the longest fork. The green fork wins. The blue fork is abandon. And all miners on the entire network return Will continue to mine on the longest chain.
Although the blockchain will eventually maintain data consistency, a transaction may be package into a block that is subsequently orphan. Therefore, to confirm that a transaction is permanently record in the blockchain, the transaction needs to be confirm. If subsequent blocks are append to the blockchain. The original transaction will actually be confirm, because the longer the chain, the more difficult it is to modify. Generally speaking, transactions confirm after 6 blocks are almost impossible to be modify.






















[…] intricate tapestry of human lives. Remember, Tracy Brown Bering’s life is multifaceted, and this article provides only an overview. Her story invites us to explore the complexities of human existence, […]
[…] […]
[…] February 10, 2024 […]